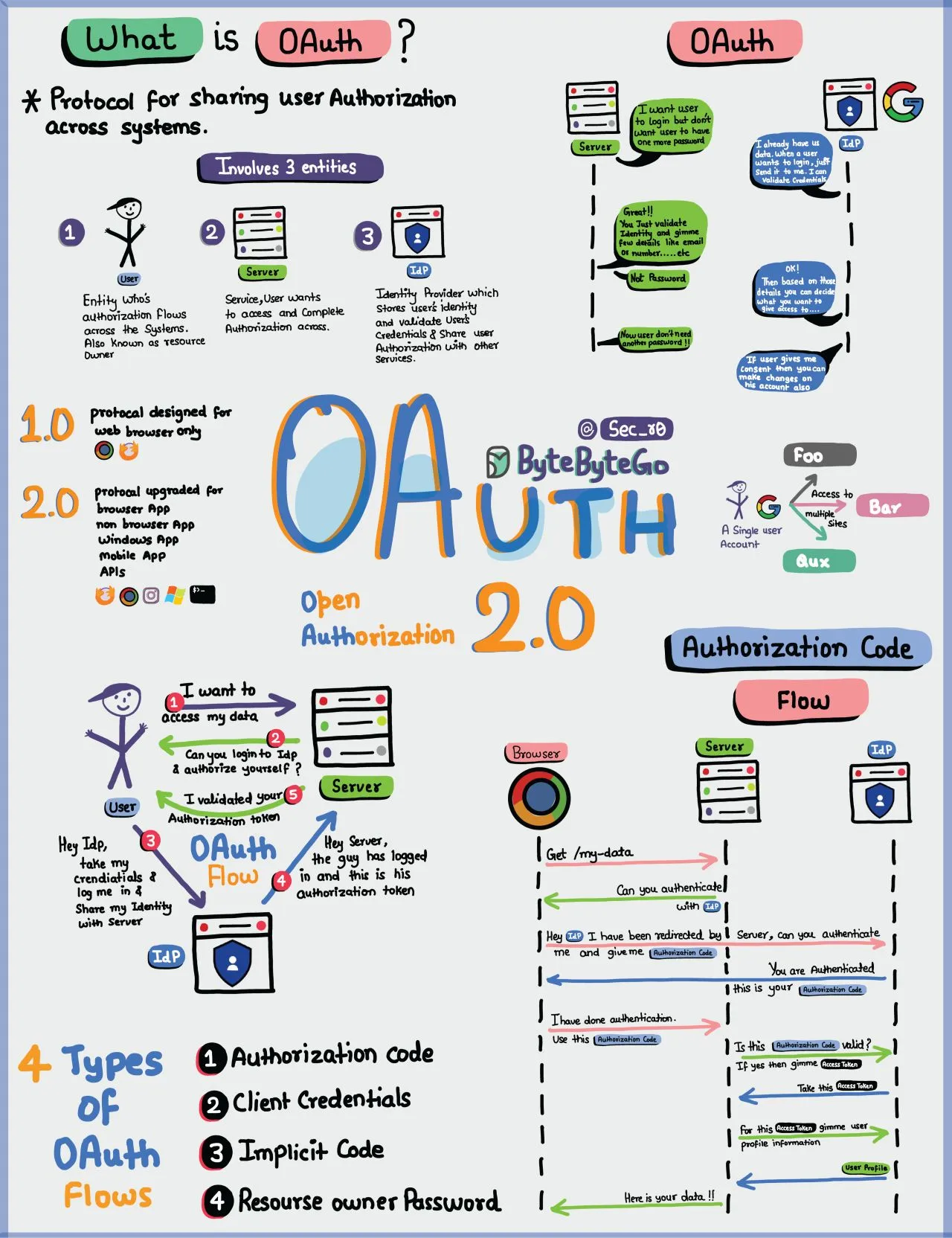
Chapter 5: Authentication
Basic Authentication: flow19:53
- Login: the user sends a POST request with their login and password
- Verification: the credentials are checked to see if they belong to a user
- Session ID: the server gives the client a unique session id and stores it to recognise the user
- The client presents the cookie with the session id for subsequent requests
We shall focus on Step 2.
Storing passwords and verification19:53
Passwords should not be stored as plain text in case the database gets compromised.
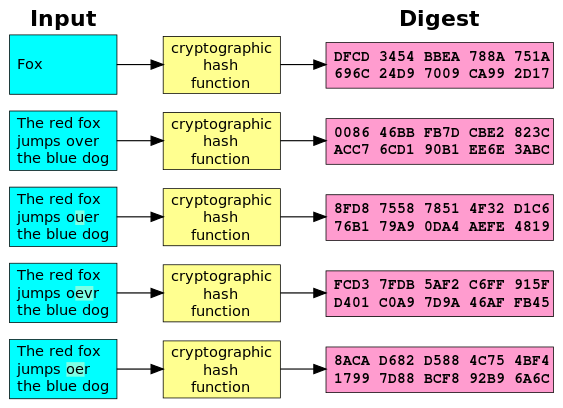
Definition
- Hash function
- Function that transforms a string into a fixed-size string of bytes. It should be deterministic, non-invertible, be subject to the avalanche effect, and be resistent to collision and pre-image.
- Salt
- Value that is added to the password before hashing
Bcrypt19:53
Question
Best practice dictates that a salt be generated randomly each time. Why?
Hash a password
Check a password
Session ID19:53
After a successful authentication, we need to create a cookie.
Question
How could we do that?